Nowadays, many companies are developing web and mobile applications, which means having logic on securing their application programming interfaces (APIs). These interfaces connect different technological systems. They are able to process queries from users, deal with server instructions and facilitate the processing of data.
APIs are the building blocks of modern applications, which can be protected in a very similar way to how regular old web applications have been protected until now.
The rise of APIs in the business ecosystem generates a need to add security layers. Since APIs deal with personal and sensitive information, an extra layer of security is crucial for every developer.
For that reason, today we want to provide you with the API Security Checklist that will help you to keep your APIs safe.
But first and before diving into the API security checklist, let’s explore the main concepts you need to know.
What is API Security?
API security focuses on protecting application layers and creating logic that takes action in case a malicious hacker tries to interact with an API. It embraces programs and strategies that allow for understanding and mitigating potential vulnerabilities and security risks of APIs.
Without a proper API security checklist, rapid innovation in web and mobile applications would not be possible, as APIs are exposing application logic and sensitive data such as Personally Identifiable Information (PII).
Why is API Security important?
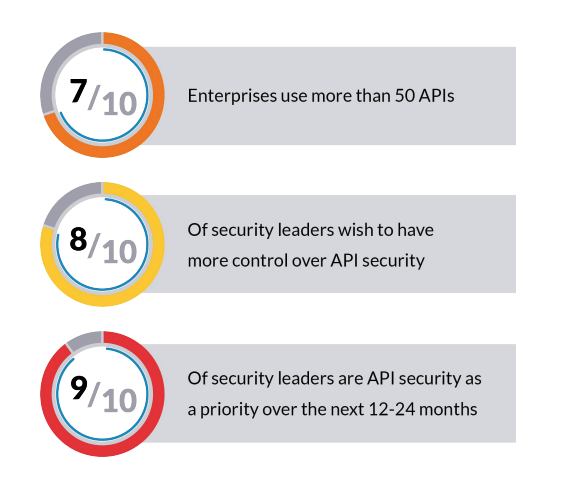
As attacks on APIs are more and more common, companies are starting to adopt security measures in order to protect their sensitive information from hackers. According to the Imvision report “API Security is Coming”, 91% of IT professionals admit that API security should be a priority in the next two years.
Research by Salt has shown that overall API traffic on its platform increased 141% while malicious traffic grew 348%. As API technology advances, the need for protecting sensitive information and data is increasing.
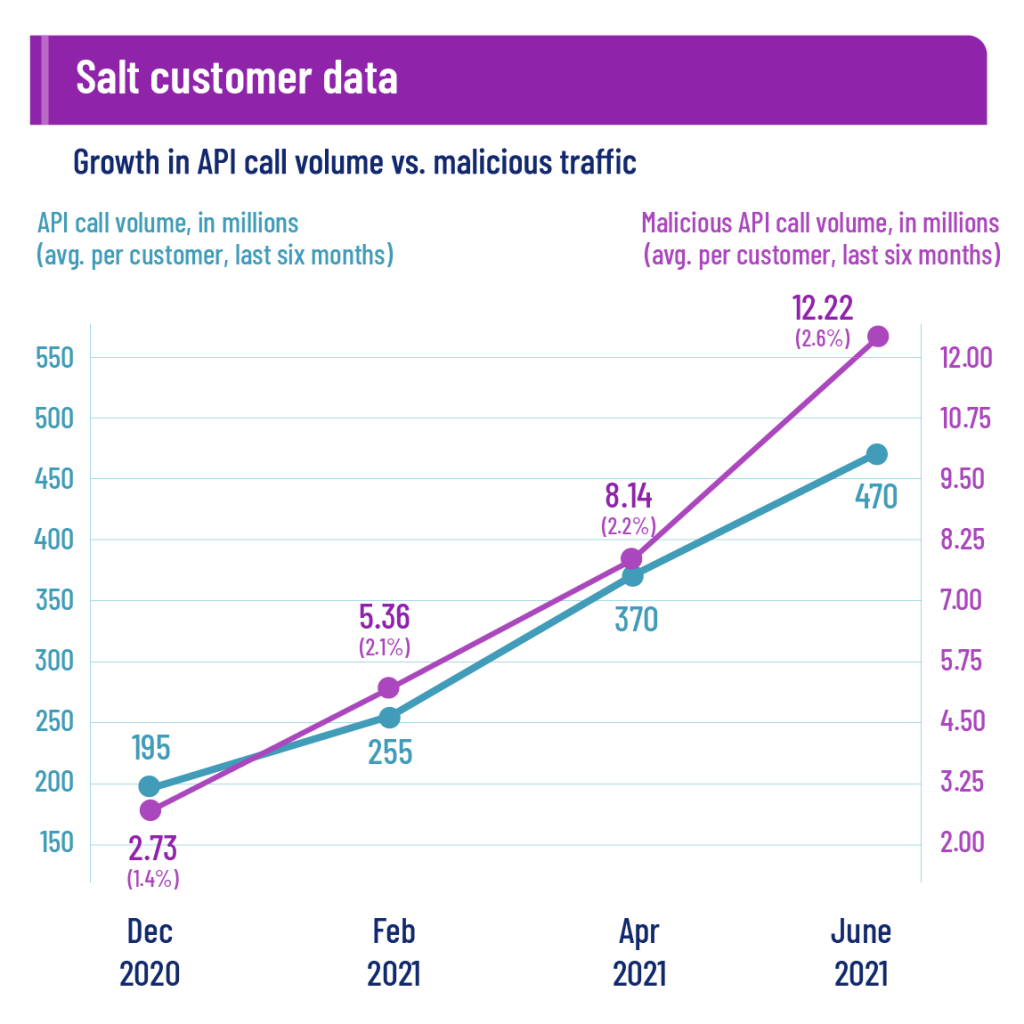
Apparently, attacks against API don’t seem to stop, so companies are beginning to take API security checklists and measures more seriously. In a new report released in the first quarter of 2021 by Imvision, it has been confirmed that 91% of IT professionals consider API security as a priority.
API Security Risks
Not surprisingly, cyberattacks have become an everyday problem in today’s cyber world. Since APIs are able to reveal apps for third-party integrations, they are more susceptible to hacker attacks, and the security strategies must be strengthened, as well as the API security checklist processes. Here are some of the most common risks APIs may have:
- Poor software development practices
Starting off with bad or inefficient coding might expose API to serious security risks. Ensure your API coding is correct from the get-go in order to avoid irreversible issues in the future.
- Issues managing APIs
In big corporations, sometimes barriers or blockers could make APIs tracking and utilization not as accurate as it should be. This can deliver the API into malicious hands, and hackers will be able to steal keys, personal information or passwords.
- XML format
XML format has some security gaps regarding its SOAP protocol. That is why it can yield several security risks that hackers can take advantage of.
- Redundant API usage
Repetitive API usage can persist if it is not properly tracked. What can we do in this case? Having a strong API administration and control can be very helpful.
API Security Checklist
At Reloadly, we truly believe that safety comes first. For that reason, we recommend all API users follow an API security checklist and transact with peace of mind knowing that the connection details are safe and sound.
Ensure your account and credentials are safe by following the API security checklist.
- Use a dedicated email ID belonging to your company domain to create your developer account.
- Choose a strong password for your developer account. Try to avoid words, phrases, and numbers while creating a new password because it can be easily found on your social media accounts. Remember that you should not reuse a password because if one of your accounts gets compromised, others can be compromised too.
- Secure your account with two-factor authentication (2FA). Two-factor authentication is a way of establishing access to an online account or computer system that requires the user to provide two different types of information. It provides the system you’re trying to access with additional evidence that you are the rightful owner of the account.
- IP Whitelisting. When you whitelist your production server IP addresses, it ensures that traffic from only those servers will be accepted by an API.
- Ensure that your ID and API Keys are in possession of very few authorized personnel only and are not shared with anyone else within or outside your company
- Make sure that your user portal password, Client ID, Client Secret and Bearer tokens are never printed to server logs and are never checked-in into version control.
API Security Best Practices
When interacting with APIs, it’s very important to observe certain security protocols to avoid having your account being compromised and vulnerable. Make sure your development team is following the API Security Best Practices while integrating with Reloadly APIs:
- Promote and encourage a strong culture around security in design and code.
- Ensure that production security credentials like passwords, clientID, client secret, etc. are never checked into version control.
- Ensure that your source code is accessible to only those who need to have access to it.
- Have your engineering team review code with your ITSM team to certify that all security policies mandated by the organization are fully implemented.
- Ensure that sensitive information such as passwords etc. is never stored in databases or files in clear-text format.
- Ensure that developer machines and servers are always patched with the latest security patches appropriate for the operating systems they run.
- Be aware of social engineering and other phishing threats.
- Ensure and demand from third-party integrators that end-to-end encryption via the latest standards of SSL/TLS is used.
- If you integrate with Reloadly APIs via server-side, ensure that your security credentials like ClientID and ClientSecret are not printed to server logs. Your production servers should be fully secure and locked down for any unauthorized access.
- If you integrate with Reloadly APIs via SDK, ensure that you have robust processes in place to manage the production clientID and clientSecret that you package in your mobile apps. Consult the relevant documents and best practices applicable for the platform you are developing for, e.g. iOS, Android.
In Conclusion
The best way to protect your API from attacks and malicious hackers is by implementing proper measures and an API security checklist. Make sure you are familiar with top vulnerabilities your API can face as understanding this will enable you to proceed with adequate methods.
If you have any questions while integrating with Reloadly API or you need more information about security best practices, you can get immediate professional help here.